Unintended Vuln in BackdoorCTF Challenges ¯\_(ツ)_/¯
Hey, I am SpyD3r(@TarunkantG) from team bi0s and the teambi0s secured 9th position in @BackdoorCTF.
In this CTF there was a lot of unintended vulns, If you talk about web then, I did Two first blood on challenges Get-Hired which had about 14 solves, and Get-hired-2 which had only 3 solves, by SpyD3r(@teambi0s), @jinmo123(CyKor), and@DefConUA.
And another team member solved Bf-Captcha as in an unintended way.
And there was also one backdoor in BackdoorCTF from that @greunion_ctf got access into their server. And because of that, they added one bug-bounty field along with the challenges.
So this CTF went off like searching any unintended way or finding any backdoor 😛
How I got unintended Vulns
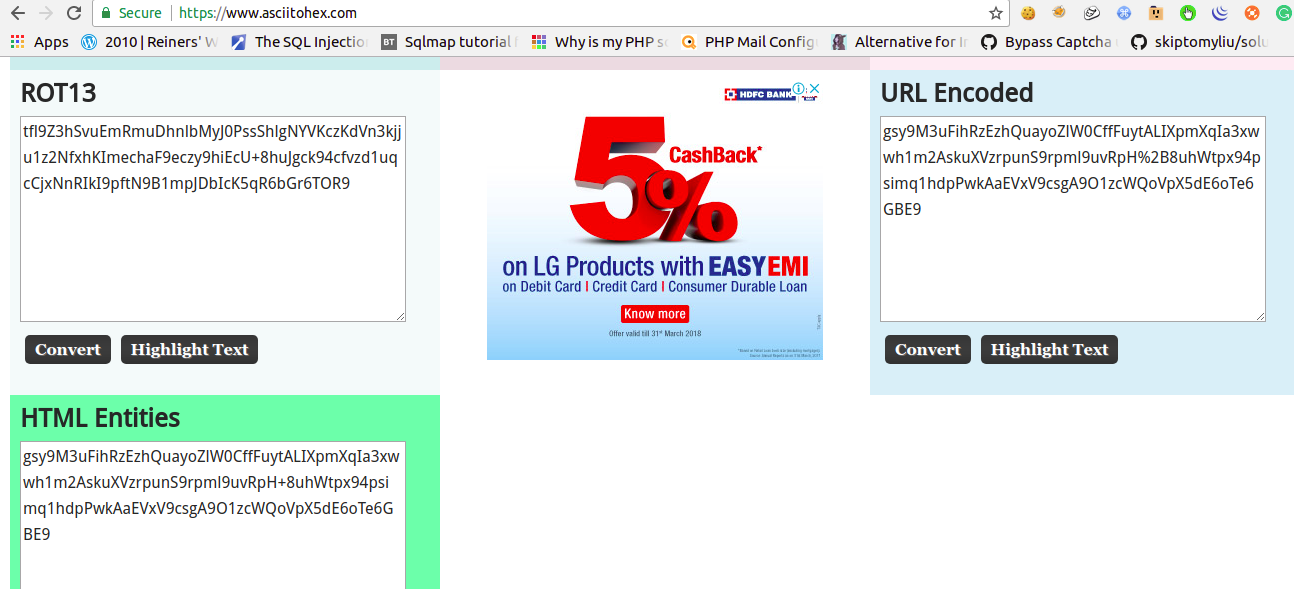
I think challenge developers was using gedit and forgot to delete Tilde files 😛
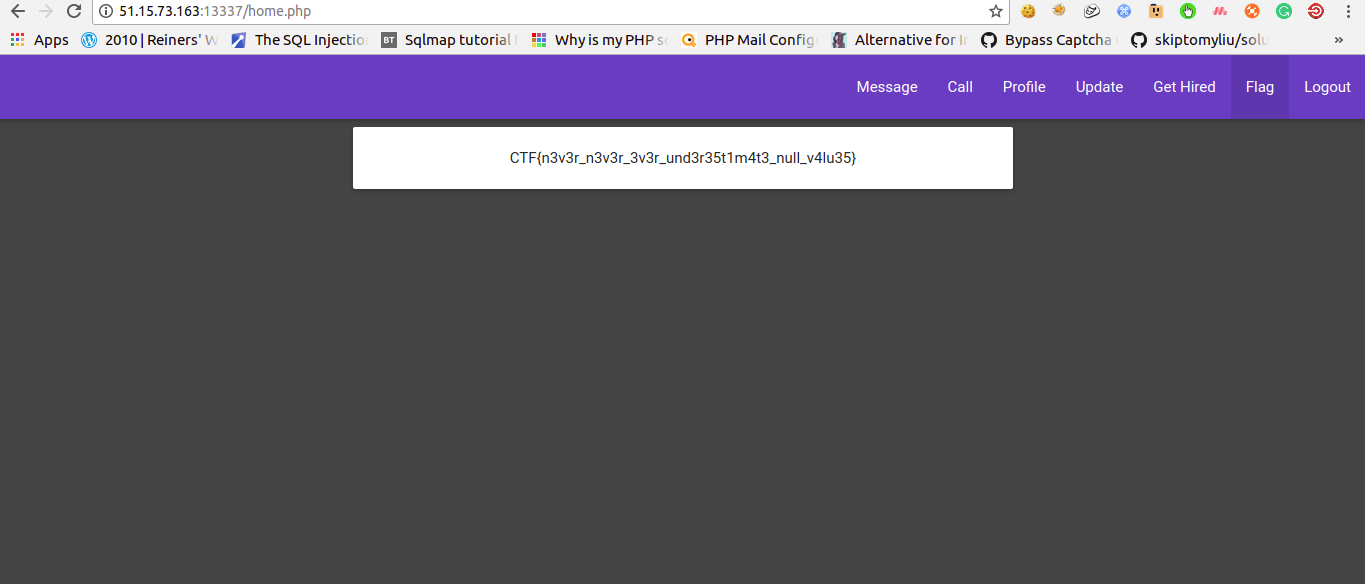
Get-Hired
https://pastebin.com/raw/VHDPJNjU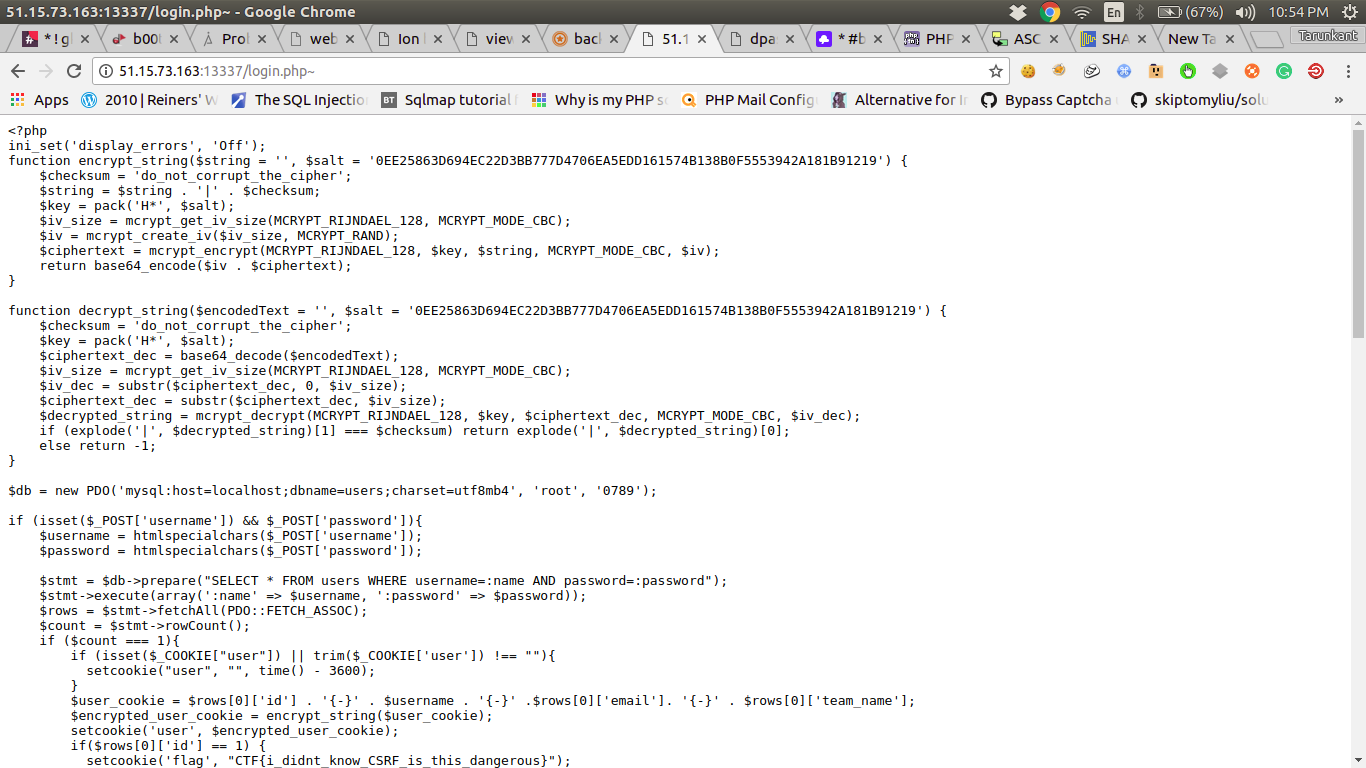
And this thing made my work too easy 😛
Now we have function for both Encryption and Decryption.
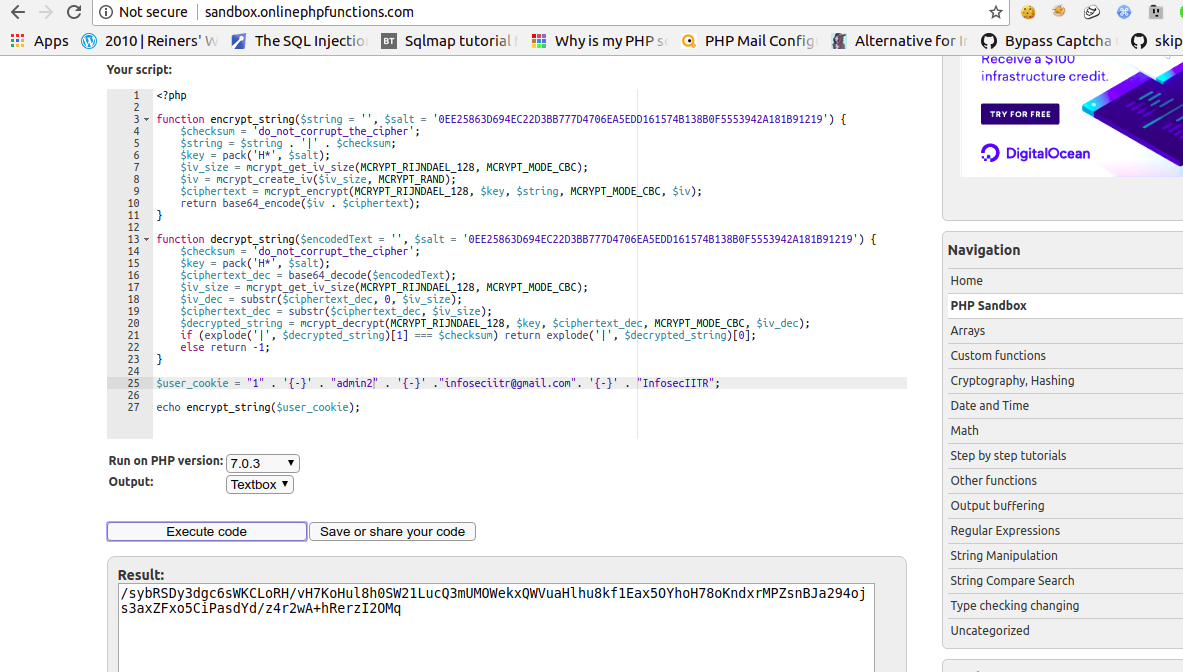
And we can see there, cookie is encrypted using encrypt_string function and one more thing to notice is :1
$user_cookie = $rows[0]['id'] . '{-}' . $username . '{-}' .$rows[0]['email']. '{-}' . $rows[0]['team_name'];
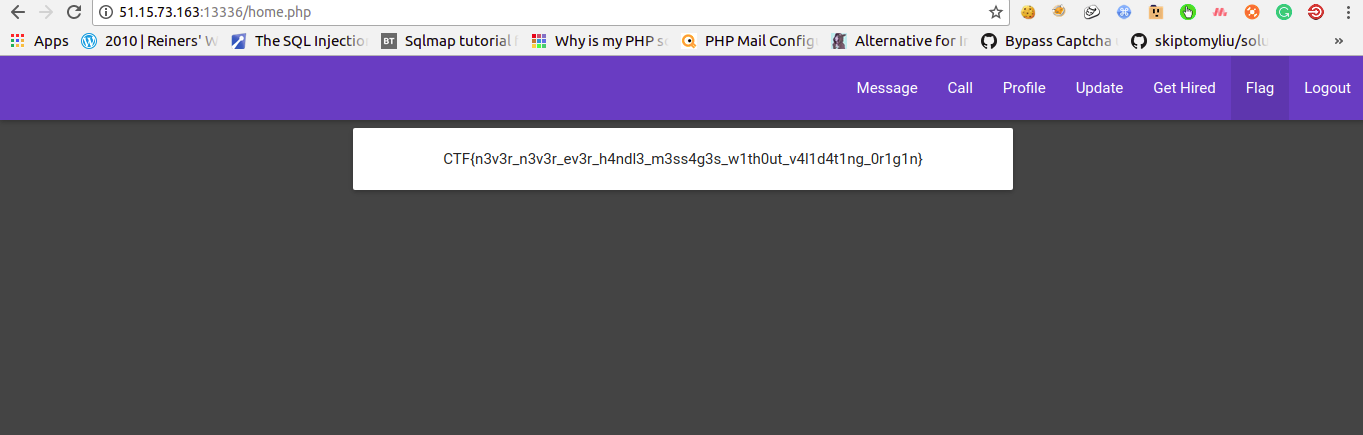
And our target is to login as “admin”.
So, we know the $username(‘admin’), and while searching for remaining details I encountered with profile section and there I got to know that I can play with id parameter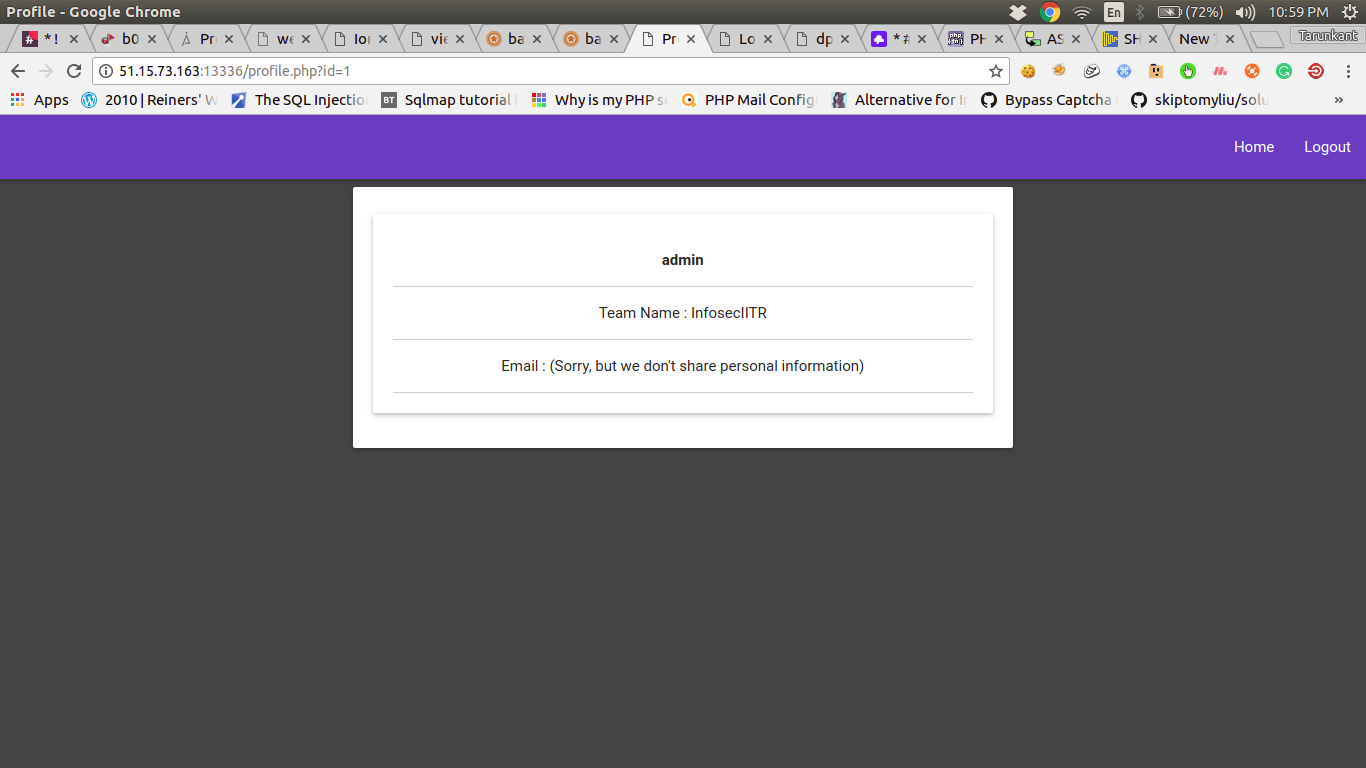
So, till now I got id , username and team_name yet to found email.
while playing more I also got to know that email is `[email protected]` .
Now what??
Just encrypt it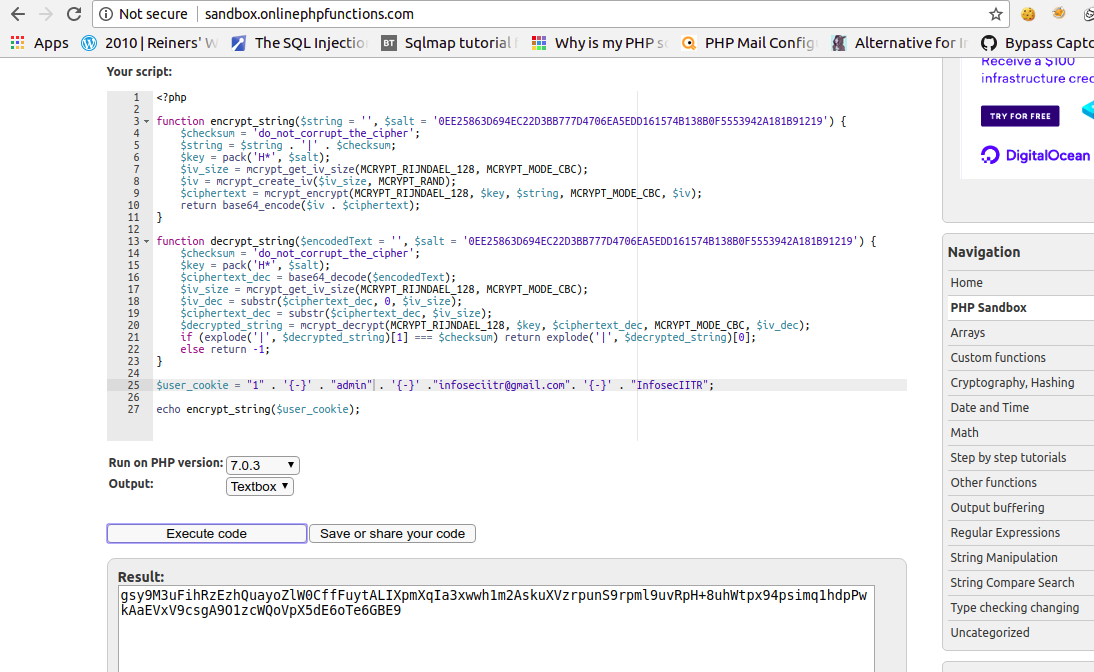
Now make it URL encoded and change user cookie to this…AND YOU DONE
Get-Hired-2
What you think now, can you do it on your own?
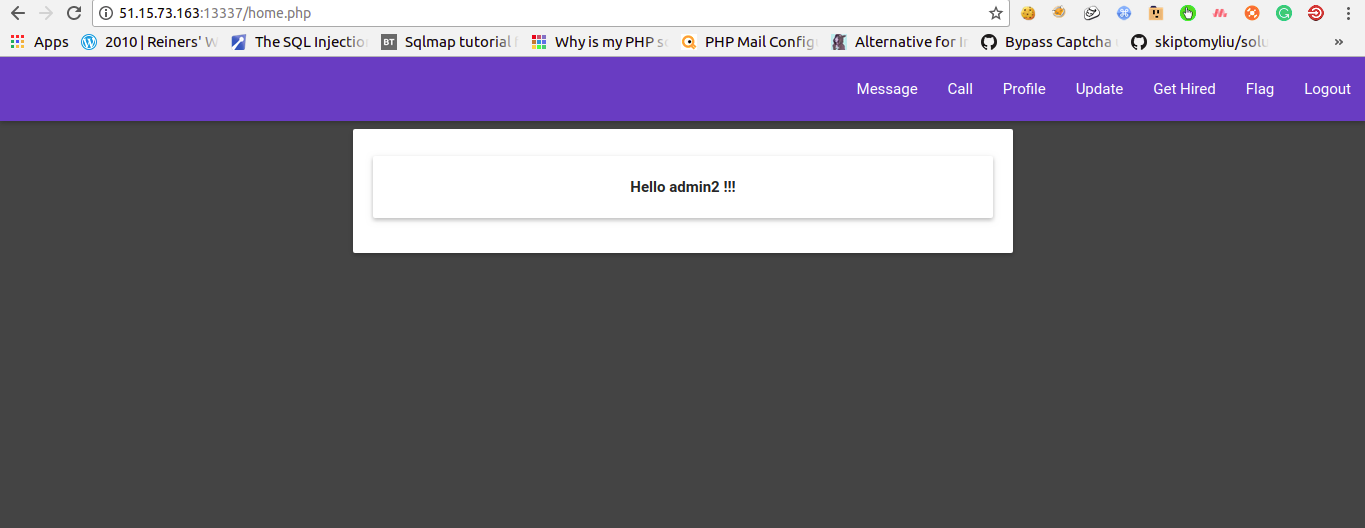
Now the challenge is asking for login as “admin2”.
And the thing is I am damn lazy, So without thinking I just changed username to “admin2” and did the same…AND AGAIN DONE
Then I was working on finding the bug in the server because there was one chall for reporting the bug and if you did it successfully then you will be rewarded with 400 pts.
Bug-Bounty
I tried but didn’t get any 😦
but what I got is here below 🙂
The source code I got from Get-Hired, discloses the MySQL Credentials.
And the funny thing was that the connection was from “root” user (Means I had creds for MySQL root user) 😛
So, I was trying to access there MySQL server:1
mysql -h 51.15.73.163 -P 13336 -u root -p
But it was not responding (It was like in the wait state)
Then I tried1
mysql -h 51.15.73.163 -u root -p
It was throwing one error :1
ERROR 2003 (HY000): Can't connect to MySQL server on '51.15.73.163' (111)
I don’t know why I was getting this error (Probably they are blocking other users, I guess so) but if anyone knows why this error came then please DM me.
And finally the CTF was good (as my team member said) but the challenge developer didn’t test the challenges, the CTF would have been better if they would have tested the challenges.
And this was the 1st time I got the 1st blood…really it was awesome feeling 😛
Thanks, for reading this blog, I hope you understood what I meant to say.